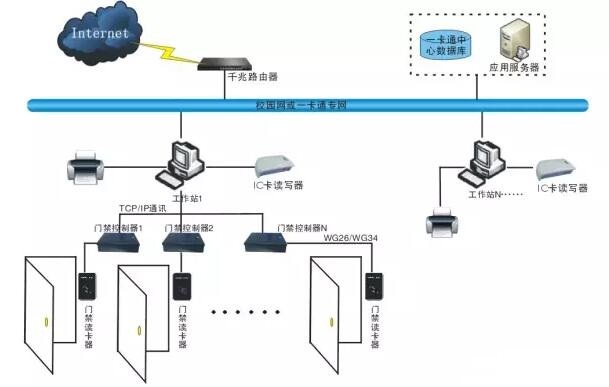
Access control card is no longer a new thing. It integrates various previously unrelated systems through identity reading, network, database and other technologies. It has its application everywhere in its present life. Access control, attendance, parking lots, etc. from buildings, communities, campuses, factories, etc. have penetrated into all aspects of society. As technology and applications evolve, it has changed the way people live. Card understanding Use a card and a platform to provide access control, parking, attendance, check-in, elevator, visitor, patrol, electronic payment and information inquiry services. The card data is stored in a database, and the card basic information is shared. The whole system realizes one card issue and one loss report, and reaches the real cartoon, Netcom, and Coton. Access control system structure The design of the access card should not be a simple combination of individual functions, but should be considered from the technical realization of the overall design ideas of the unified network platform, unified database, unified identity authentication system, data transmission security, various management system interfaces, exception handling and other software. To make the overall performance of each management system and each terminal equipment to the best design. The Access Card can implement a variety of different management functions. These functions should be able to use devices from different manufacturers, as long as the cards in the same format are used. The advantage of this application mode is that it can select products with higher degree of specialization and suitability for individual functions for each function, and there is no incompatibility problem. One subsystem failure should not affect other subsystems and system platforms. At present, suppliers such as Card Intelligence have enabled the card to be applied in various enterprises, schools, or projects, and even form a real cross-regional or cross-industry application. As the most common security subsystem in security intelligent systems, it has been widely used in government, enterprises, finance, hospitals, military and other industries, and can be integrated and linked with other intelligent systems, such as burglar alarm, video surveillance, fire protection. Alarms and building automation systems. Although the access control card system is still evolving, it has matured from technology to application. This can roughly summarize the typical subsystems of the five aspects of the access control card from the products of various manufacturers: 1 platform management: rights management, equipment management, data management, card management and other subsystems; 2 identification: access control, ladder control, attendance, patrol, vehicle access, vehicle commuting, conference sign-in, visitor management, storage management and other subsystems; 3 electronic transactions: banking circle storage system, consumption management system, water control management, electronic control management and other subsystems; 4 information services: WEB query, touch screen query, telephone voice query, SMS query and other subsystems; 5 integrated access: ERP interface, library management interface, educational management interface, human resource interface, office automation system, can provide OPC interface and other video surveillance, alarm, fire, building automation system and other integration. Typical platform architecture The access control card can be divided into two parts: the basic platform and the business application. The basic platform provides data access support and the business application implements business processing. Each business application shares a basic platform, and each service of the basic platform can be invoked in the scope of authorization, and the business application can be freely increased, decreased, and expanded. On this platform, other functional modules can be added or removed easily, flexibly and freely. At present, most card systems adopt a standard three-layer structure: physical equipment layer, application operation layer, and information service layer. The physical layer can adopt RS-485 bus or TCP/IP, and the application layer and the shared layer all adopt TCP/IP network. Such a network structure can meet the requirements of transmission stability, security, flexibility and the like. The advanced bus and information integration technology integrates the management subsystems in the card management system on a basic platform and forms information resource sharing through the internal INTRANET network. Based on the "service layer + application layer + device layer" mode, there are currently two types of typical architectures for access control cards: The first category: TCP/IP+ bus architecture, the bus can be RS485, CAN, etc. Each subsystem has an independent management server, which is connected to the terminal controller via the bus under the management server to realize the professional functions of each subsystem. Each professional management server is connected to the service layer subsystem and the application layer subsystem via the TCP/IP network, and has functions such as platform database, card management, and rights management at the service layer, and various query subsystems at the application layer. This kind of architecture should be said to be the most widely used in the industry, and it also presents a more stable and mature architecture. This type of architecture extension is also more convenient, as long as the professional management server is added in the TCP/IP layer, and then the bus is connected to the professional terminal control device. The architecture is also more convenient to integrate with third-party systems, such as other video surveillance, alarm, fire, building automation systems. There are two types of integration methods. The switch quantity linkage can be directly input and output through the access control terminal control device, which is very simple. The other is pure software linkage, which is linked with the access control card platform via TCP/IP by means of the corresponding system server. The second category: full TCP/IP architecture, including terminal controllers are all network-type. All device layers, service layers, and application layer devices are hung on the TCP/IP network. Service layer subsystems and applications of this type of architecture. The layer subsystem is the same as the first type of architecture, and the management server of the corresponding subsystem is not connected to the professional controller by bus. Everyone exchanges data by TCP/IP. The architecture is as convenient as the integration of the third-party system, and the switch quantity can also be directly input and output through the access control terminal control device, and the other pure soft linkage is also linked by the management server of the corresponding system via TCP/IP. Overall, compared to the previous pure 485 bus system, TCP/IP system has the following advantages: 1) Fast transmission speed, making full use of TCP/IP network transmission advantages; 2) The system application and expansion are flexible and convenient, compatible with the 485 bus structure, and each subsystem is accessed by module; 3) The user interface is friendly, easy to install and use; 4) It can reduce large-scale wiring based on the user's original computer network, and is suitable for large-scale and ultra-large-scale applications; 5) Improve the maintainability of the system, and the IP network facilitates remote diagnosis and maintenance. Basic function appeal The mature access control card system should have the characteristics of high reliability, high scalability, large capacity, etc., so as to be suitable for complex application environments, unified management of multiple applications, and technical features that can gradually introduce new applications. 1) High reliability: High reliability of access control includes field device reliability, system security, and data reliability. Equipment reliability means that the system hardware equipment must withstand the test of complex use environment (such as adapting to high temperature difference environment, anti-inductive lightning attack and poor quality of installers); and because the system is based on TCP/IP network transmission, terminal controller and upper layer The inter-platform network transmission should adopt a special encryption algorithm to ensure the security and reliability of the transmitted data. Although the upper management platform adopts a unified database, it should be able to provide multiple sets of application systems to ensure data reliability. 2) Scalability: Access control card works under a network and software and hardware platform, which supports a unified operating system and database, and adopts the "service layer + application layer + device layer" architecture mode, distributed application, centralized Management is the principle of its composition and operation. Therefore, in addition to the unified management of access control, attendance, parking, visitor system, consumption, etc., the card platform can also ensure that the system can be easily accessed (including hardware and software) such as elevators, visitors, conference attendance, electronic patrols. Subsystems. In addition, in the intelligent system integration application, the card platform should have an open standard interface, which can be easily combined with other subsystems (video surveillance, burglar alarm, perimeter alarm), fire alarm system, building automation system, office automation. Integration of systems, industry-specific business systems, etc. 3) Large capacity: Now the access control card system has been applied in various fields, such as enterprises, schools, communities, etc. The large capacity of the system is the key and basic guarantee for the unified management of multiple systems. For example, some large enterprises need to be able to manage all kinds of information of tens of thousands of people, while traditional systems can only support hundreds or thousands of people. Taking Card Smart Access Card as an example, its access controller can support up to 40,000 offline information storage, high-speed computing can guarantee the response time of the card is only 0.1-0.2S, and its alarm upload is transmitted to the alarm workstation only within 2S. That is to say, only such a stable large system can meet the needs of various applications. Technical development characteristics Referring to the products of the main door-to-door card manufacturers in the industry, the following trends are summarized in the technical direction: 1) Multi-layer distributed network structure: The future access control card will develop to such a network structure, which is convenient to use, stable and reliable, high in security, resource sharing, flexible in expansion, easy to maintain, fast response, and high efficiency. Advantage, so the system will be more suitable for application and expansion, and more reliable. 2) B/S architecture: The C/S architecture has separate client software that needs to be installed on the management computer, and the B/S architecture only needs to be configured on the server, and then managed and controlled through the WEB webpage access on the operating computer. This improves the flexibility and convenience of the system, but for large systems, system settings and so on still need C / S architecture support, B / S architecture for direct user operations, both are indispensable. 3) Configuration software: various functional modules are rich, software performance is stable, with good openness, authority control, etc., making security and security more rigorous, and the visual style interface is more intuitive and user-friendly. 4) Security: For the information transmission and data storage of front-end identification, control processing, network communication and other aspects, strict encryption technology (such as national secret, 3DES) is adopted to ensure high security of system data storage and transmission. 5) Certified diversity: Supports various biometric technologies such as IC cards, CPU cards, composite cards, fingerprints, and faces. As a "portable" and "unique" authentication medium, biometric authentication, together with card media, will definitely develop rapidly in the card application. In addition, smart card multi-certification, smart card + password authentication, biometric + card authentication and other composite authentication modes will be applied according to security level and environmental requirements. In addition, there are some special authentication modes that have also been proposed and gradually formed products such as SMS temporary authentication and voicemail authentication. The internal user enters a specific number on the card reader. After the system confirms, a random code is automatically generated and sent to the user's mobile phone by SMS to realize functions such as identity verification and door opening, and the automatic use fails once. In addition, the user can dial the special service number of the card center by telephone, and according to the voice prompt operation, the system determines the user specific code and the input password to implement identity verification, and records related events in the system for query. 6) Database: In the future, the one-card platform can support various database structures such as ORACLE and SQLserver to improve the applicability of the system database. 7) Mobile phone card: All the functions of the IC card (including M1 and CPU) are integrated on the mobile phone card, so that the mobile phone card has all the functions of the traditional card while retaining all the functions of the original communication, and can also be derived. A lot of features that traditional one-cards don't have. 8) Cloud technology: This technology brings a remote card, cloud-based card, whose core goal is to realize real-time local and inter-regional information of users at any time and any place through cloud storage and remote software applications. At the same time, it simplifies the installation, commissioning and operation and maintenance of the system. Cloud services streamline the development of unified backends that connect existing applications, data and services to any PC, tablet and phone. 9) Integrate or become mainstream with access control as the platform: In the current security industry, video surveillance is the main body to integrate access control and alarm, but it is foreseeable that with the continuous development of access control technology, the access control system is the main body to integrate video. Systems and other systems such as alarms and fire protection will also become a trend. Because the access control system is characterized by active defense and more and more functions, the access control system can accommodate more systems, and it can better integrate many security systems. Conclusion Access control card is a system that completes device control through card authentication. From the initial single door ban, it has gradually become a card widely used today, and almost everything can be involved. From the current application point of view, it has derived a number of subsystems such as attendance, visitors, patrols, conference sign-in, consumption, goods circulation, parking lot access, elevator control, etc., and with the expansion of personnel identity certification, item certification and other requirements, System applications will continue to expand. As an important part of the intelligent system, the access control card should also be an open system. It can be integrated with IBMS, BAS, OA and other systems through standard interface protocols such as OPC and SOCKET to realize linkage with video surveillance, fire alarm and equipment management. And realize the data synchronization with the unit management system, that is, through the data integration between the systems, the access control card can truly play the role of maximizing. Perfume shower gel,Milk Bath Shower Gel,Oily skin shower gel Guangzhou Berfly Cosmetic Co., Ltd , https://www.berflycosmetic.com